Author: Dirk Shaw
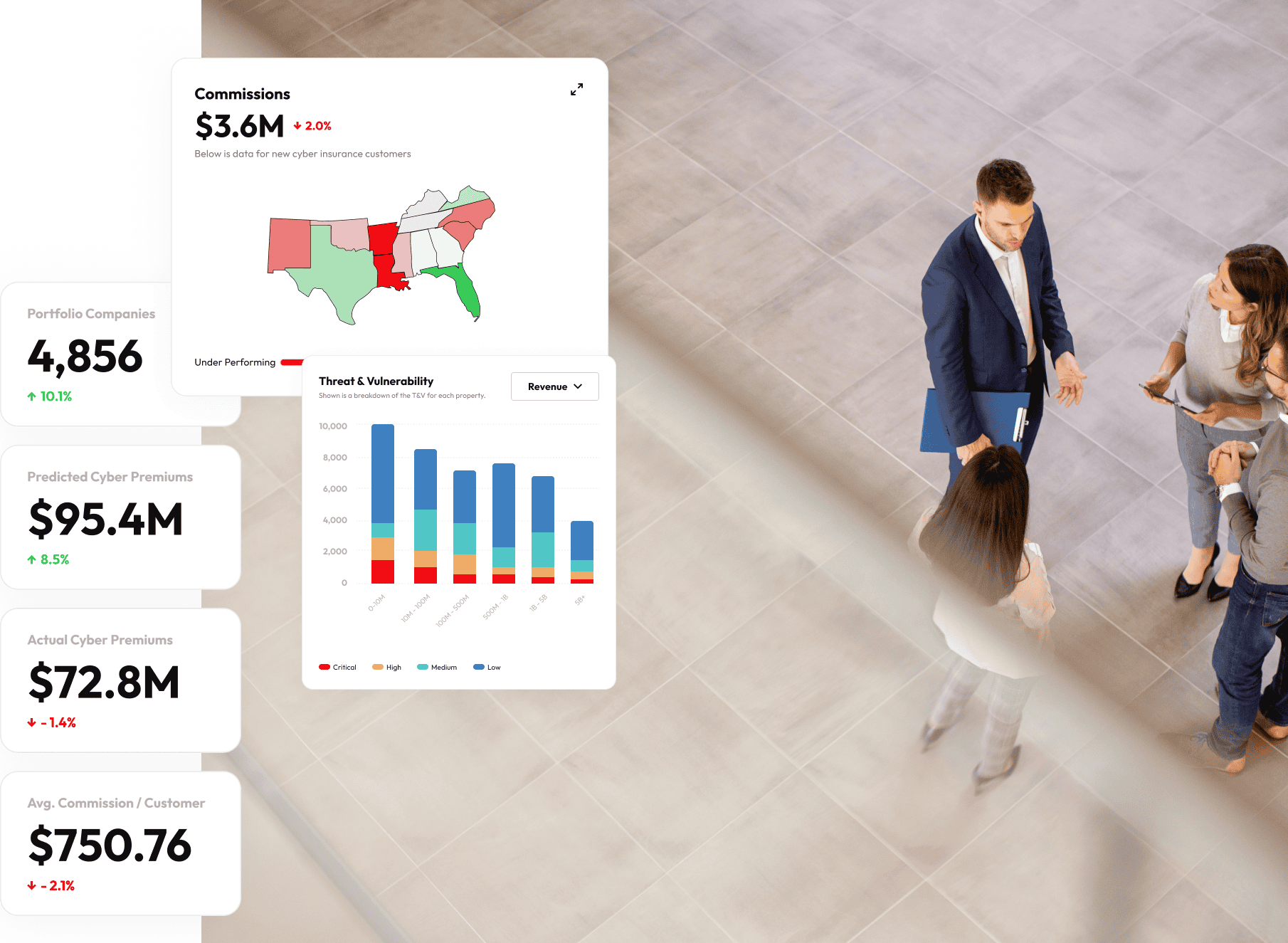
In the intricate world of cyber insurance, brokers face the dual imperative of carving out a larger market share while […]
In late March, Risk & Insurance caught up with Reuben Vandeventer, CEO of SecondSight. What follows is a transcription of that discussion, edited […]
The digital landscape is evolving rapidly, presenting a complex array of risks that challenge traditional risk management practices. In response, […]
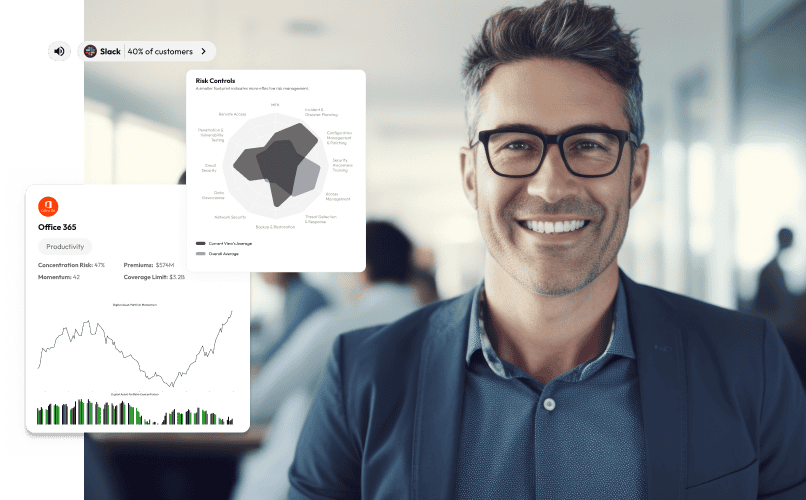
In the intricate world of cyber insurance, brokers face the dual challenge of staying abreast of the latest threats while […]
In the evolving digital landscape, Chief Financial Officers (CFOs) face two pressing questions: How can artificial intelligence (AI) be harnessed […]

The Path to Integrated Digital Transformation: A Broker Executive’s Compass As the landscape of cyber insurance is poised for unprecedented […]

As the cyber insurance market gears up for a staggering growth, projected to leap from $15 billion to between $30 […]

Excerpt from a recent Webinar with Insuretrust — As the landscape of technology continues to evolve, Artificial Intelligence (AI) has […]

As I continue to explore the journey of digital transformation within the insurance brokerage sector, I need to look ahead […]

Having spent over a decade crafting digital experiences for some of the most iconic consumer brands, I’ve witnessed firsthand the […]